
Nozomi Networks Threat Intelligence continuously updates Guardian sensors with rich data and analysis so you can detect and respond to emerging threats faster.
Guardian correlates Threat Intelligence information with broader environmental behavior to deliver maximum security and operational insight.


Threat Intelligence provides continuously updated and detailed threat information.
Up-to-Date Threat Intelligence
Extensive Threat Risk Indicators
Provides detailed threat information:
OT and IoT Threat Insights
High Performance for Fast MTTD
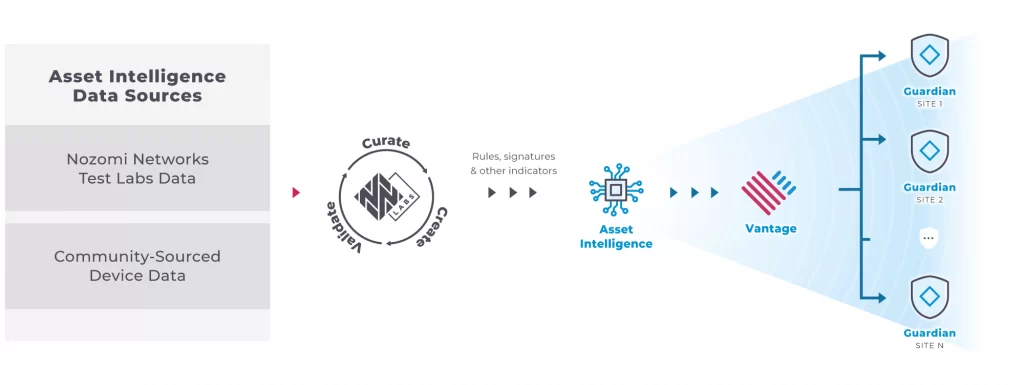
Accurate Asset Intelligence
Detailed, Helpful Alerts
Simplified IT/OT Security Processes
Fast Forensic Analysis
Continuous threat research reduces response the time to detect active threats and vulnerabilities.

Threat Intelligence Feed is broken into several data sources and formats for a range of OT, IoT and ICS threats, source information and IOCs.
Open and Interoperable
Our Threat Intelligence Feed can be used outside our Guardian and Vantage platforms, with other third-party security products. This data feed can be used by any security platform that handles industry-compliant Structured Threat Intelligence eXpression (STIX) and Trusted Automated eXchange of Intelligence Information (TAXII) threat data, both of which are open data formats for threat details.
More Flexibility to Detect Emerging Threats
The feed delivers a single, unified source of data, including malicious IP addresses or URLs, new indicators of compromise (IOC) signatures, threat sources, malware hashes, and methods and tactics to gain system access. All these serve to accelerate incident response and enhance security operations.
One example use case involves feeding the Nozomi Networks threat data into Azure Sentinel SIEM to identify new IOCs. Then, a Security Orchestration, Automation and Response (SOAR) platform updates a Palo Alto Networks firewalls with new isolation rules based on the IOCs.
Discover how easy it is to anticipate, diagnose and respond to cyber threats and process issues before they impact your operations.


Εγγραφείτε στην επικοινωνία της
i-metrix για να μαθαίνετε πρώτοι τις προσφορές και τα νέα μας.
E-mail: info@i-metrix.gr
T: +30 210.300 2050
Ad: 20-22 Tzortz st. | Athens | GR