Cyber Protect Cloud
#imetrixexpert

Cyber Protect Cloud
#imetrixexpert
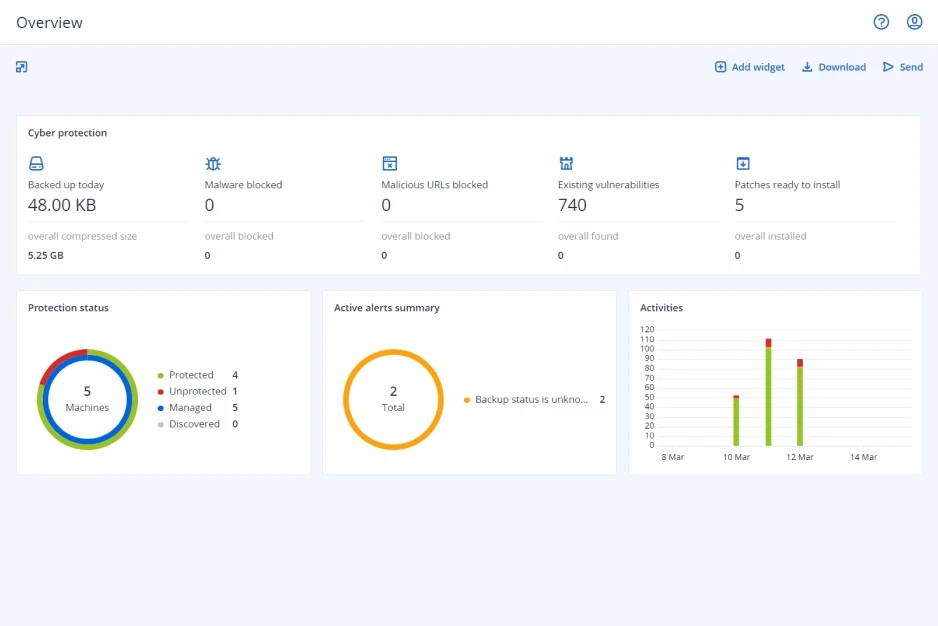
Minimize your security risks with integrated cyber protection covering 100% of their workloads and unlock unique capabilities not available from your current security vendor. Rise to the challenge of 2021’s cyberthreats and greatly reduce security incidents and breaches. Leverage the solution that’s a leader in independent testing (VB100, AV Test, AV-Comparatives, ICSA Labs).
Add other powerful components to strengthen your services even further with advanced protection packs and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
Enhance your security services with integrated cyber protection that includes full-stack anti-malware. Increase your detection rate and responsiveness to the latest cyberthreats. Extend cyber protection to web browsing, backed-up data, the recovery process, and exploit prevention. Enable investigations by capturing forensic data in backups.

Anti-Malware Testing Standards Organization member

VirusTotal member

Cloud Security Alliance member

Anti-Phishing Working Group member

Microsoft Virus Initiative member

CRN 2020 Partner Program Guide: 5 Star Data Storage and Backup Vendors
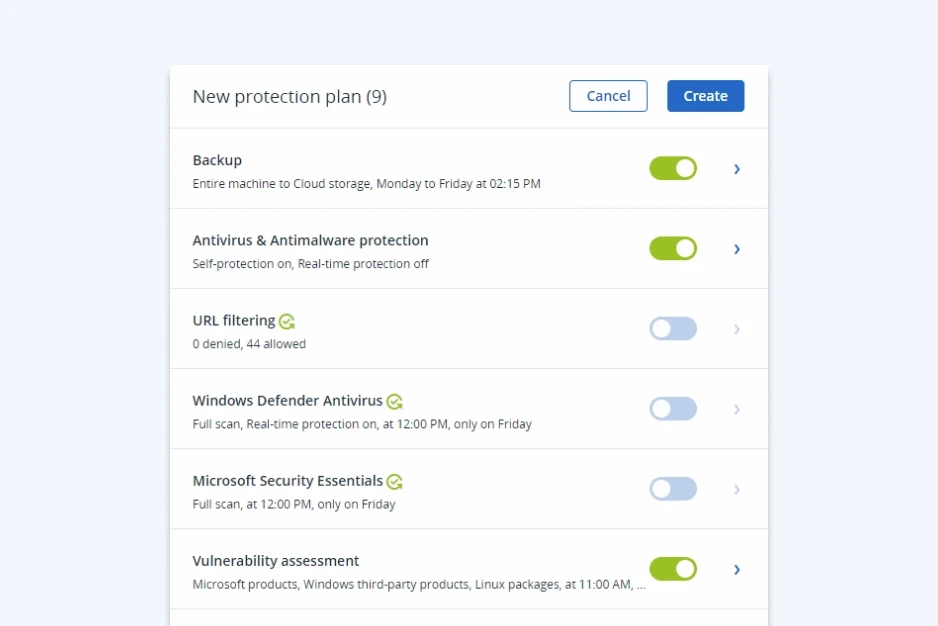
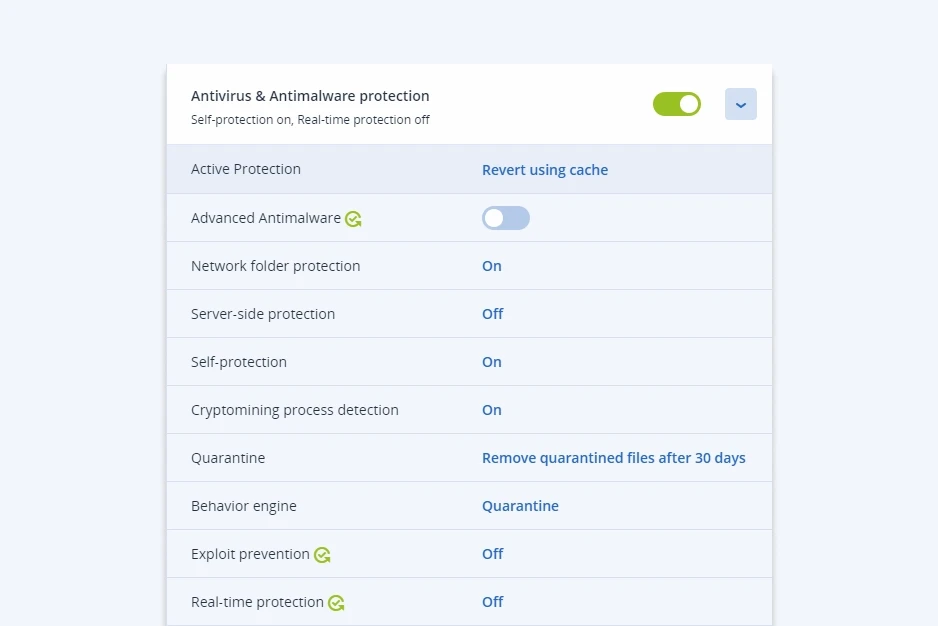
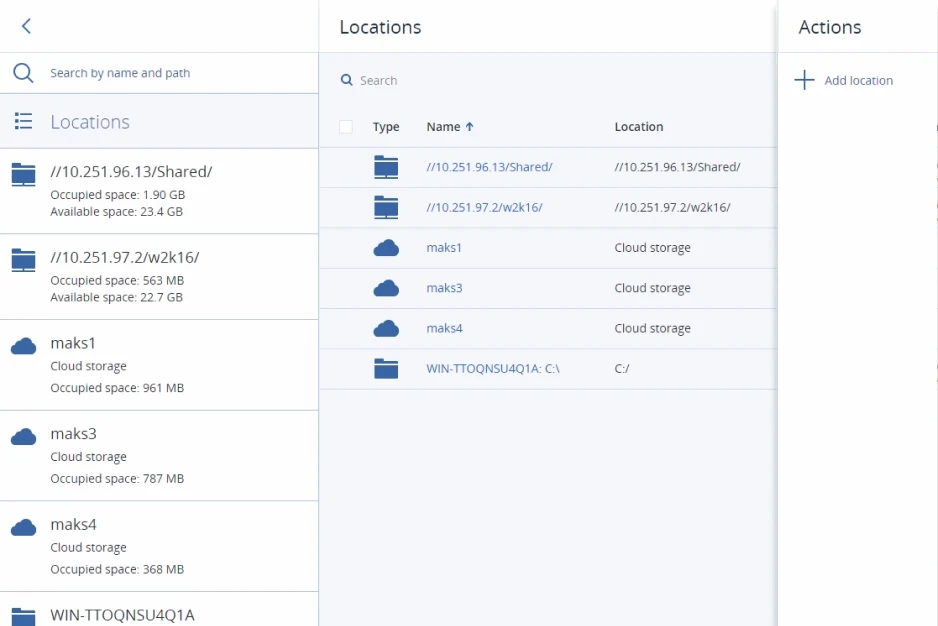
Includes all features of Acronis Cyber Backup Cloud
The Business Resilience System (BRS), purpose-built for Acronis Cyber Protect Cloud, takes delivery operations resiliency and end-to-end data protection to a whole new level.




Acronis Cyber Protect Cloud with Advanced Backup Overview
To deliver thorough protection for our partners’ clients, Acronis’ vision and products are based on a multi-stage process rather than simply detecting and blocking threats, leaving other risks uncovered.






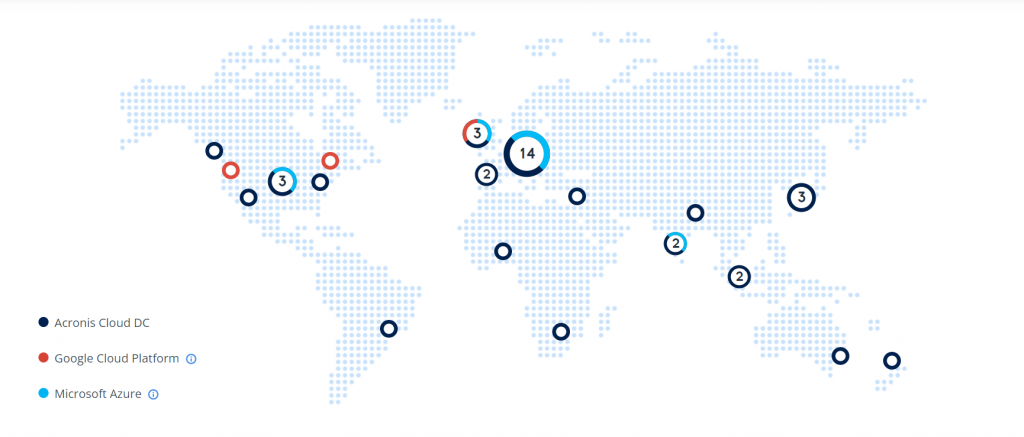
Help your clients meet their unique needs by storing their data where they choose. With multiple data centers worldwide, Acronis enables you to meet the compliance, data sovereignty, and performance requirements of all your clients.


Εγγραφείτε στην επικοινωνία της
i-metrix για να μαθαίνετε πρώτοι τις προσφορές και τα νέα μας.
E-mail: info@i-metrix.gr
T: +30 210.300 2050
Ad: 20-22 Tzortz st. | Athens | GR