Stop Data Breaches at the Endpoint
#imetrixexpert

Stop Data Breaches at the Endpoint
#imetrixexpert
provides unrivaled protection against accidental disclosure and theft of sensitive data and critical assets from trusted and untrusted (malware, APT) users.
Rather than restricting devices that connect to the cloud/network and passively audit data transfers, the GTB Advanced Endpoint Protector offers organizations the ability to control what content can be transferred between the network, applications & removable media devices – both on and off-premises, including cloud applications. With the unique ability to ACCURATELY detect, investigate, and respond to data exfiltration attempts, many enterprises use GTB for DLP, EDR & UBA instead of 3 different vendor tool-sets.
Secure intellectual property, sensitive data, and meet regulatory compliance quickly with out-of-the-box and custom policies, applying unique market-leading DLP detection capabilities to control data theft on Mac, Windows & Linux.
is data that is saved on removable media devices. GTB’s Endpoint Protector scans data for sensitive content before it is saved and then can block unauthorized transfers. The Endpoint Protector can also detect activities such as copy and paste, or use of sensitive data in an unapproved application, such as someone encrypting the data in an attempt to bypass the Endpoint Protector’s block.
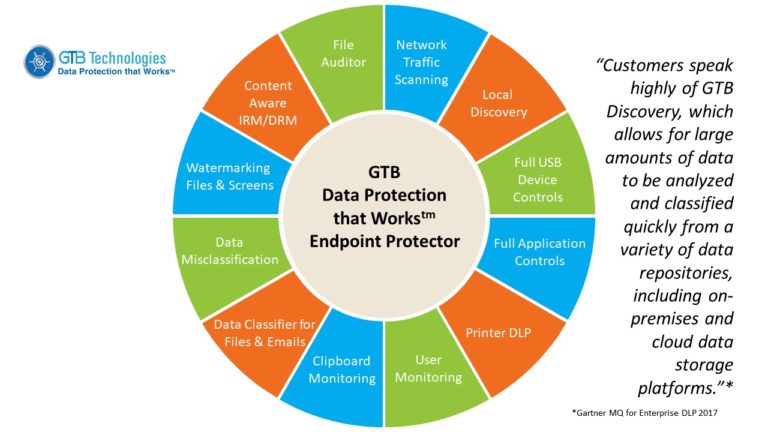
The GTB Endpoint Enterprise DLP / EDR client monitors I/O activity, enforcing access policies created in the management console. All data sent to removable media is intercepted and inspected by the GTB inspection engine. Various enforcement actions can then be taken, such as blocking, alerting, classify, watermark, encryption, etc.
Features
• LDAP Integration
• Files Encryption
• Detailed File Auditing
• Detailed Hardware Auditing
• Two-way file control … Off-premises printer controls
• Real-time Forensics
• Detailed Hardware Auditing
• Online and Offline modes – even for SSL encrypted data
• Printer DLP – with off-premises control
Actions
• Block
• Classify
• Log
• Watermark
• Encrypt
• Shadow
• Audit plus File Share DLP – the system controls access and monitors file share activities
Supported Devices & OSx
• USB Drives
• Wireless Interfaces such as Wi-Fi
• FireWire
• Mac • Windows • Linux. KEXT-less DLP
• Other I/O devices
• POS System devices
Apps & Cloud Control
• Cloud Apps / Cloud Storage
• Drop Box
• BOX
• Citrix ShareFile, QQ
• Gtalk, Google Drive, Google for Work
• Evernote, Microsoft Office 365, Teams, Salesforce, Skydrive, Slack, Snippet
• File Share Utilities (FUT) including:
Advanced MIP support and much more!


Εγγραφείτε στην επικοινωνία της
i-metrix για να μαθαίνετε πρώτοι τις προσφορές και τα νέα μας.
E-mail: info@i-metrix.gr
T: +30 210.300 2050
Ad: 20-22 Tzortz st. | Athens | GR