Whether you’re consolidating visibility and risk management at the edge or in the cloud, the CMC is fast and simple to deploy.

Whether you’re consolidating visibility and risk management at the edge or in the cloud, the CMC is fast and simple to deploy.
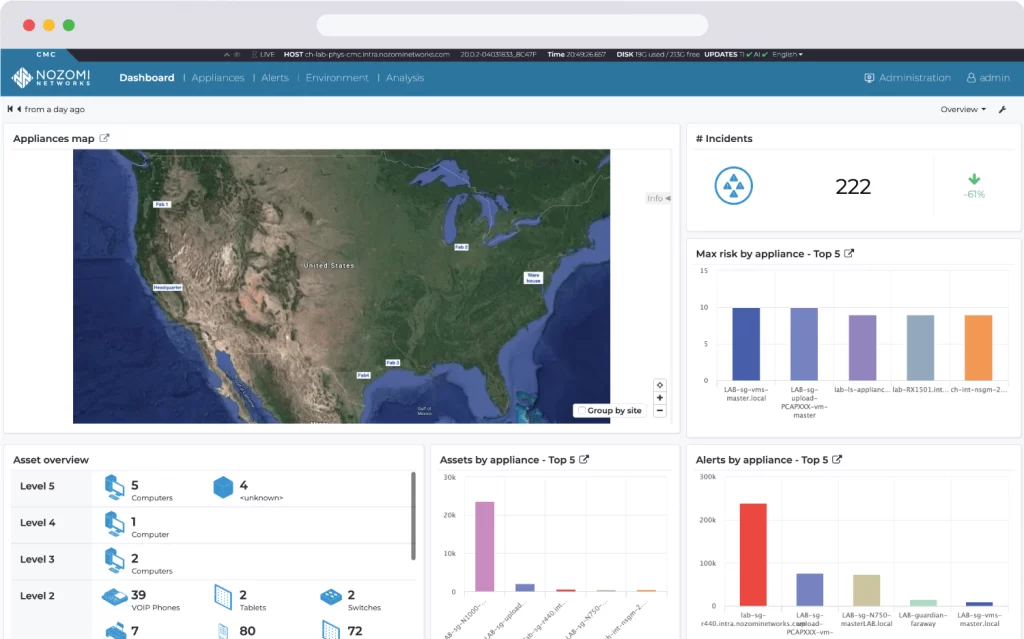
The CMC showing a geographic map of your Guardian appliances.
Single Console Access from the Cloud or at the Edge
Enterprise OT/IoT Risk Monitoring
Unified Security Monitoring
Enterprise-level Best Practices
Real-time Network Visualization
Flexible Navigation and Filtering
Summarized Asset Information
Drilldown to Individual Assets
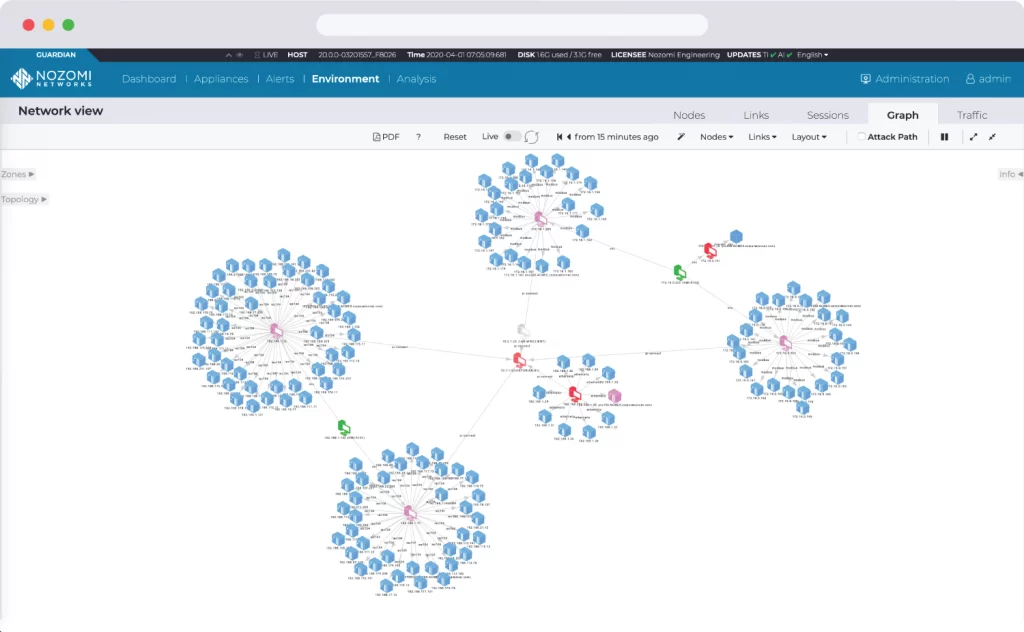
Portion of interactive Network Visualization Graph.
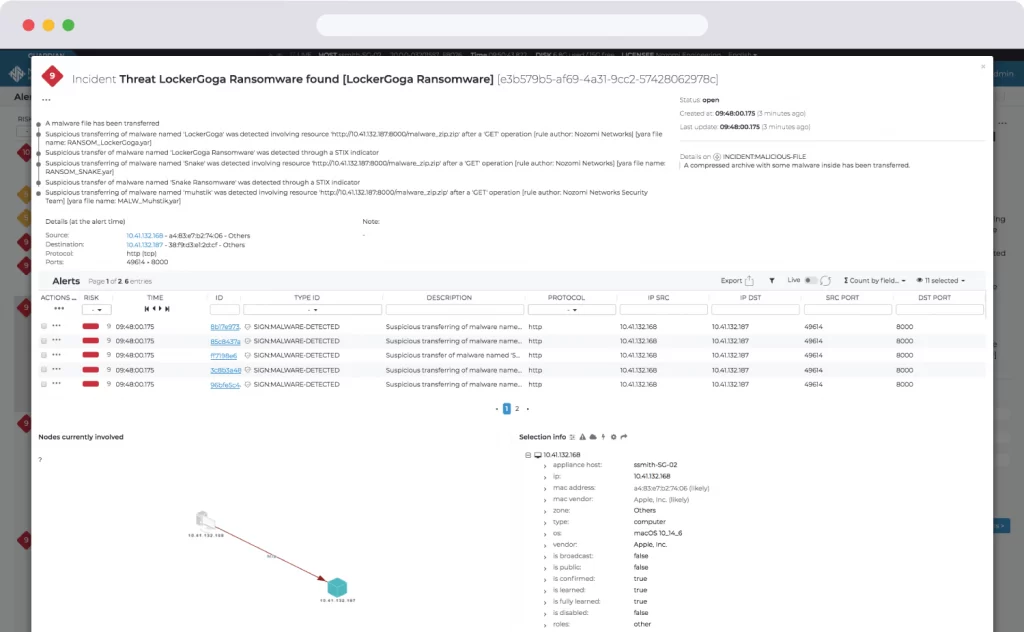
Smart Incident showing related alerts and security context.
Detect and Disrupt Emerging Threats
Unified OT and IoT Threat Detection
Powerful Tools for Fast Analysis
Smart Incidents Speed Forensics
Centralized Monitoring of OT Risks
High Availability, High Security
Swift Deployment
Immediately Valuable
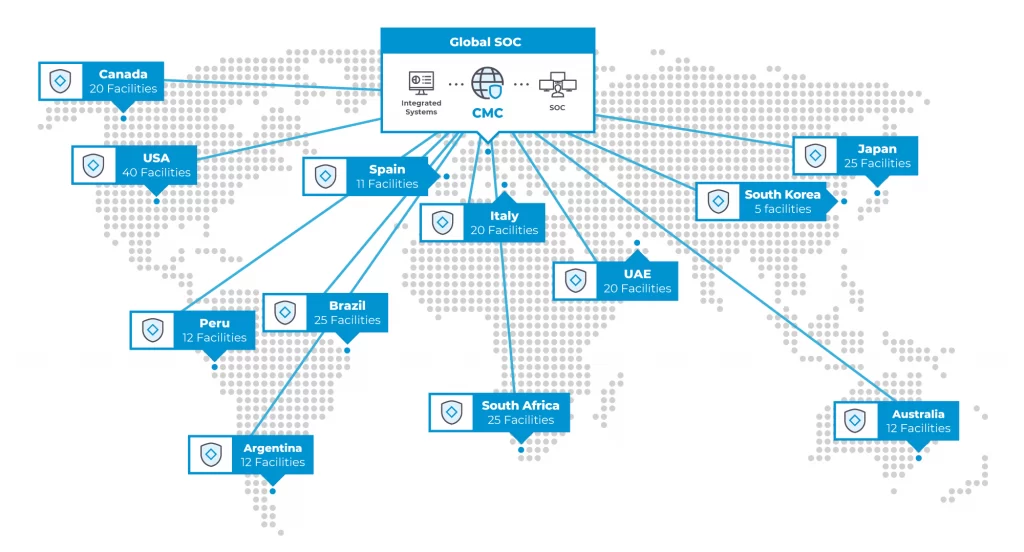
Continuous threat research reduces response the time to detect active threats and vulnerabilities.
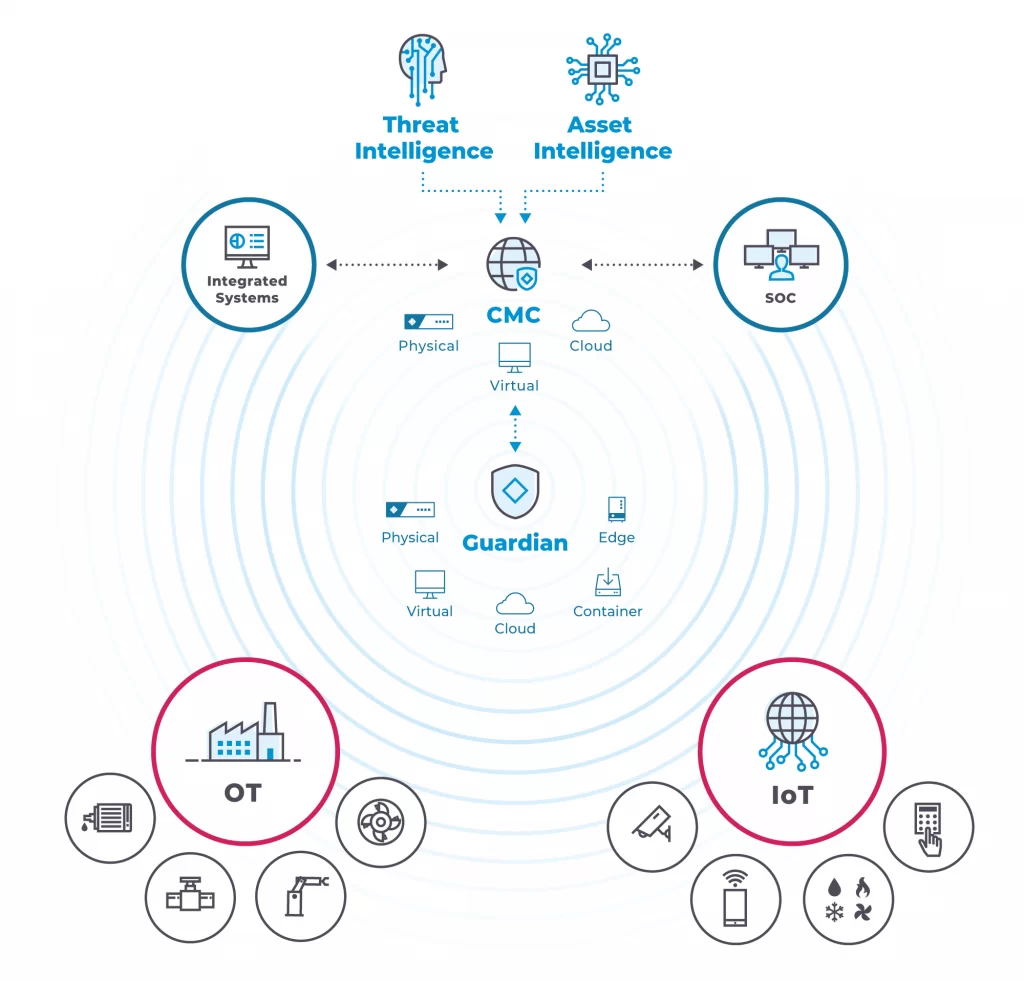
You can protect a wide variety of mixed environments with rapid asset discovery, network visualization and accelerated security.
You can tailor the Nozomi Networks solution to meet your needs by utilizing its flexible architecture and integrations with other systems.
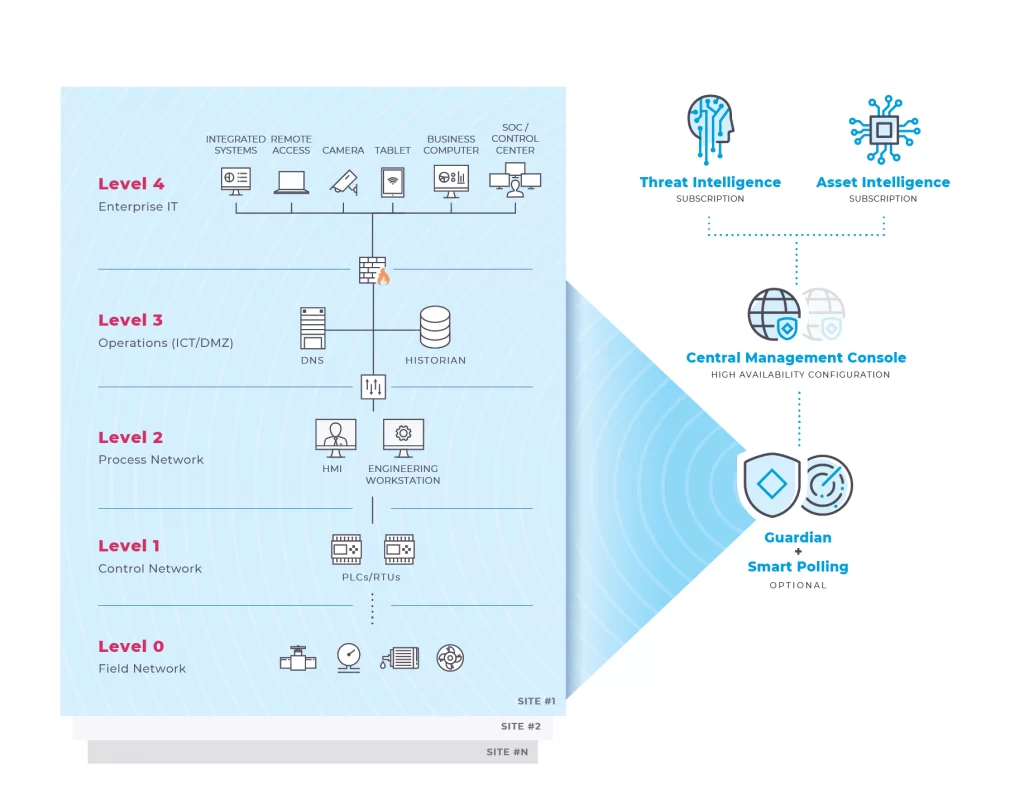


Discover how easy it is to anticipate, diagnose and respond to cyber threats and process issues before they impact your operations.


Εγγραφείτε στην επικοινωνία της
i-metrix για να μαθαίνετε πρώτοι τις προσφορές και τα νέα μας.
E-mail: info@i-metrix.gr
T: +30 210.300 2050
Ad: 20-22 Tzortz st. | Athens | GR